
Contents
Introduction
Now that we’ve covered the essentials, it’s time to level up. This part dives into advanced AWS networking components that enable connectivity beyond your VPC. We’ll explore Internet Gateways, NAT Gateways, AWS PrivateLink, Transit Gateways, VPC Peering, and VPC Endpoints. These services are key for connecting to the internet, integrating with other VPCs, and accessing AWS services securely. As applications become distributed and span multiple networks or regions, understanding these tools becomes vital for any developer.
Articles in this series
Before reading this article, I recommend that you read the previous articles in this series to understand the basics of AWS Networking.
![]() AWS Networking for Developers: Part 1 – Core Components
AWS Networking for Developers: Part 1 – Core Components
![]() AWS Networking for Developers: Part 2 – AWS Global Network
AWS Networking for Developers: Part 2 – AWS Global Network
![]() AWS Networking for Developers: Part 3 – Advanced Connectivity
AWS Networking for Developers: Part 3 – Advanced Connectivity
![]() AWS Networking for Developers: Part 4 – DNS, Load Balancers and Content Delivery
AWS Networking for Developers: Part 4 – DNS, Load Balancers and Content Delivery
![]() AWS Networking for Developers: Part 5 – Monitoring and Troubleshooting Tools
AWS Networking for Developers: Part 5 – Monitoring and Troubleshooting Tools
![]() AWS Networking for Developers: Part 6 – Developer Best Practices
AWS Networking for Developers: Part 6 – Developer Best Practices
Internet Gateway (IGW) and NAT Gateway
An Internet Gateway enables internet access for instances in public subnets. In contrast, a NAT Gateway allows instances in private subnets to initiate outbound connections to the internet (for things like OS updates or third-party API calls) without exposing them to inbound internet traffic. Developers must understand the role of these gateways to design secure yet functional networking flows. These gateways rely on route tables to direct traffic, and their correct usage is crucial in scenarios where security and external communication are both required.
Internet Gateway
An Internet Gateway is region-specific and is attached to a single VPC in that region. It provides internet access to resources in public subnets. Since the VPC is regional, the IGW can serve any public subnet in any Availability Zone (AZ) within that VPC.
Developers Uses Cases
- Hosting Public-Facing Apps – Deploying a web application or API backend that needs to be accessible globally.
Example: Your team launches a React frontend hosted on EC2 with a public IP for testing. - Direct Package/Dependency Downloads – Development EC2 instances that pull npm, pip, Maven packages, or OS updates directly from the internet.
- Webhook Endpoints – Building services that must receive callbacks from external systems like GitHub, Stripe, or Slack.
- Testing from Real Clients – Simulating real-world user access to your dev or staging environment before going live.
NAT Gateway
A NAT Gateway is Availability Zone-specific. When you create a NAT Gateway, you must choose a subnet in a particular AZ. For high availability, it’s recommended to create multiple NAT Gateways in different AZs and route traffic accordingly from private subnets in each AZ.
Developers Use Cases
- Secure Backend API Calls – Your backend app in a private subnet calls external APIs (e.g., payment gateways, OAuth providers) without exposing itself publicly.
- Private DB Migrations & Updates – Running migrations where your database server needs to download patches or sync data from a secure remote location.
- Build & Deploy Pipelines – Private build servers (like Jenkins in a private subnet) pulling code or dependencies from GitHub or Docker Hub.
- Controlled Internet Access – Keeping application servers isolated from direct inbound traffic while still allowing outbound internet traffic for updates and integrations.
AWS PrivateLink, VPC Peering, Transit Gateway
These components enable communication between VPCs or services across accounts and regions. Developers should use these options to securely integrate microservices, partner services, or shared platforms across environments. These components depend on route table configurations, DNS, and interface endpoints to function correctly.
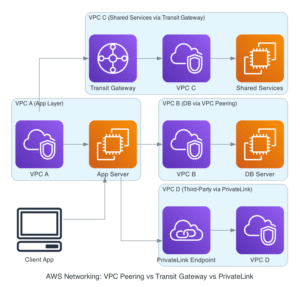
AWS PrivateLink
AWS PrivateLink is a networking service that enables secure, private connectivity between VPCs and AWS services or third-party SaaS offerings—without exposing traffic to the public internet. It allows developers to access services via private IP addresses within their own VPC, significantly improving security, latency, and compliance.
PrivateLink is a game-changer for developers who need to build or consume APIs and services in a secure, private, and compliant way. Whether you’re integrating with AWS services like S3, or exposing your own backend microservice to other teams or accounts, PrivateLink ensures that data never leaves the AWS network. It’s ideal for regulated industries, sensitive workloads, or environments where public exposure is a risk.
Use Case 1: Accessing a Third-Party API Without Public Internet
Imagine you’re integrating with a third-party SaaS billing system hosted on AWS. Instead of sending sensitive payment data over the public internet, you can connect directly to the provider’s VPC through AWS PrivateLink, ensuring traffic stays within the AWS backbone.
Use Case 2: Internal Microservices Across Accounts
In a multi-account setup, you might have a shared authentication microservice in one account and multiple apps in others. PrivateLink lets each app call the service privately without needing VPC peering or route table changes, reducing complexity and exposure.
VPC Peering
VPC Peering is a networking connection between two Amazon Virtual Private Clouds (VPCs) that enables them to communicate with each other using private IP addresses, as if they were part of the same network. VPC peering is non-transitive, region-specific (unless using inter-region peering), and does not require a VPN or gateway.
VPC Peering is critical when you’re developing applications that span multiple VPCs. For example, one VPC for frontend APIs and another for backend databases or shared services. It’s also useful in multi-team or multi-tenant environments where different services are isolated by VPCs but still need to talk to each other. As a developer, understanding VPC peering helps you design modular, secure, and scalable applications that adhere to the principle of least privilege.
Use Case 1: Merging Services Across Teams
Two development teams own separate VPCs—one runs an API, the other a frontend web app. With VPC Peering, you can connect them so the frontend calls the API using private IPs, without internet gateways or NAT.
Use Case 2: Shared Development Resources
If you run shared dev tools (e.g., Jenkins, GitLab) in one VPC, you can peer it with multiple team VPCs to allow secure, low-latency access to build and CI/CD resources.
Transit Gateway
An AWS Transit Gateway (TGW) is a centralized hub that connects multiple VPCs and on-premises networks through a single gateway, simplifying network architecture and management at scale. Think of it as a cloud router that enables any-to-any communication between connected networks, overcoming the non-transitive limitations of VPC Peering.
For developers building microservices, multi-account, or multi-region applications, Transit Gateway simplifies the backend network connectivity. It reduces the complexity of managing multiple peering connections and enables service-to-service communication across isolated environments. It also ensures scalability and flexibility in hybrid architectures where cloud services need to interact with on-premises resources.
Use Case 1: Scaling Multi-VPC Architectures
In a large enterprise with dozens of VPCs (across accounts and regions), Transit Gateway acts like a central router, removing the complexity of managing multiple VPC peering connections. Developers can build apps that need data from multiple systems without manually managing mesh connections.
Use Case 2: Hybrid Cloud Development
If you have on-premises dev/test environments and AWS workloads, Transit Gateway can link them via a single VPN or Direct Connect attachment—allowing developers to use the same tools, databases, and APIs seamlessly across both environments.
AWS PrivateLink vs VPC Peering vs Transit Gateway
| Feature / Decision Factor | AWS PrivateLink | VPC Peering | Transit Gateway |
|---|---|---|---|
| Primary Use Case | Secure, private access to specific services without exposing traffic to the internet | Direct network connection between two VPCs | Centralized routing for many VPCs and on-premises networks |
| Traffic Scope | Service-to-service (via ENI) | Full VPC-to-VPC routing (private IPs) | Any-to-any routing between attached networks |
| Best For Developers When… | You need to call an internal API or a third-party service privately | You need low-latency access between two dev environments or apps | You work in a large environment with many interconnected systems |
| Number of Connections | One endpoint per service | One peering connection per VPC pair | One attachment per VPC, scales to hundreds |
| Cross-Account Support | Yes, easy to set up | Yes, but more manual | Yes, built-in multi-account support |
| Cross-Region Support | Yes | Yes (additional setup required) | Yes |
| Routing Complexity | No routing table changes required | Requires adding routes to each VPC's route tables | Centralized routing, no VPC-to-VPC route management |
| Internet Exposure | None (private AWS backbone) | None (private AWS backbone) | None (private AWS backbone) |
| Developer Example | Call a payment API securely in another account | Access a shared dev database from another team’s VPC | Connect dev, staging, and prod VPCs plus on-prem tools |
VPC Endpoints (Gateway and Interface)
VPC Endpoints allow private connections to AWS services without traversing the internet, enhancing security and reducing latency. Gateway endpoints are used for S3 and DynamoDB, while Interface endpoints are used for most other services. Developers should use VPC endpoints when building secure, high-performance applications, especially in regulated environments. They interact with route tables and security groups and are essential for controlling egress traffic from private subnets.
Gateway Endpoints (S3, DynamoDB)
A Gateway Endpoint is used to route traffic to AWS services within the AWS network, avoiding the public internet.
Developer Use Cases:
- Data Pipelines to S3 – When running ETL jobs (e.g., AWS Glue, EMR, Lambda) that read/write large volumes of data to S3, a Gateway Endpoint ensures low latency, high throughput, and no internet exposure.
- DynamoDB-based Applications – For serverless apps using DynamoDB, a Gateway Endpoint allows EC2, Lambda, or ECS tasks in a VPC to securely connect without NAT Gateway costs.
- Secure Analytics Workloads – Data analytics clusters (Athena, Redshift Spectrum) pulling S3 datasets can use Gateway Endpoints for faster and more secure access.
Interface Endpoints (Powered by AWS PrivateLink)
An Interface Endpoint creates an elastic network interface (ENI) in your VPC for private connectivity to supported AWS services or your own services.
Developer Use Cases:
- Private API Access – Developers can connect to AWS services like SSM, CloudWatch, or API Gateway without exposing traffic to the public internet.
- Third-Party SaaS Integration – When integrating with a partner service that supports AWS PrivateLink, you can securely connect from within your VPC without a VPN.
- Internal Microservices – Host internal APIs using PrivateLink so other teams or VPCs can consume them without setting up peering or Transit Gateway.
- Regulated Workloads – In industries with strict compliance (finance, healthcare), developers can ensure all API calls happen over private IP addresses.
For example, Lambda functions configured to execute inside a VPC cannot access other AWS services directly. S3 and DynamoDB are global services that are accessed through public endpoints. One way to access these services from VPC-bound Lambdas is to attach a NAT Gateway to the VPC and enable public access to AWS Services. This is less secure as it allows all public Internet access to the Lambda function. The most secure way is to create a Gateway endpoint with the Prefix List of each of these services and attach it to the VPC. This ensures that the AWS Services are accessible to the Lambda functions while ensuring the functions do not have public Internet access.
Key Differences
| Feature | Gateway Endpoint | Interface Endpoint |
|---|---|---|
| Purpose | Primarily for accessing S3 and DynamoDB | Supports a broader range of AWS services, including S3, DynamoDB, and others |
| Cost | Free | Hourly and data transfer charges |
| Services | S3, DynamoDB | Broad range of AWS services |
| Access | Within VPC only | Within and outside VPC |
| Architecture | Route tables | AWS PrivateLink (ENI) |
| Cross-region | No | Yes |
| Example | Connecting instances in a private subnet within a VPC to S3 buckets without needing an Internet Gateway or NAT Gateway | Securely accessing S3 from an on-premises network or from a peered VPC in another region |
Conclusion
Mastering AWS’s advanced connectivity services empowers developers to design cloud architectures that are not only functional but also secure, scalable, and cost-efficient. By understanding when to use services like PrivateLink, Transit Gateway, VPC Peering, and the various gateway options, you can fine-tune network flows, minimize latency, and ensure your applications meet business and compliance requirements. These tools aren’t just about connecting components, they’re about connecting them the right way for optimal performance and security. As your workloads grow more complex, the ability to choose and combine these services effectively will be a defining skill in building resilient cloud solutions.


[…] AWS Networking for Developers: Part 3 – Advanced Connectivity […]
[…] AWS Networking for Developers: Part 3 – Advanced Connectivity […]
[…] AWS Networking for Developers: Part 3 – Advanced Connectivity […]
[…] 🔗 https://thedeveloperspace.com/aws-advanced-connectivity/ […]