
Contents
Introduction
In today’s cloud-native world, applications are no longer confined to a single server or data center. They are distributed, scalable, and dynamic. As a developer, understanding how networking works in the cloud is no longer optional; it’s essential. AWS provides a robust set of networking services that empower developers to build secure, high-performance, and resilient applications.
When building on AWS, understanding how your infrastructure communicates is crucial. Every cloud application begins with the network. At the heart of AWS networking is the Virtual Private Cloud (VPC), a logically isolated environment where developers build secure, scalable systems. This part lays the groundwork for everything to come, covering CIDRs, VPCs, Subnets, Route Tables, Security Groups, Network ACLs and Elastic IPs. Whether you’re building a monolith or microservices, understanding these components is essential to defining and protecting your infrastructure.
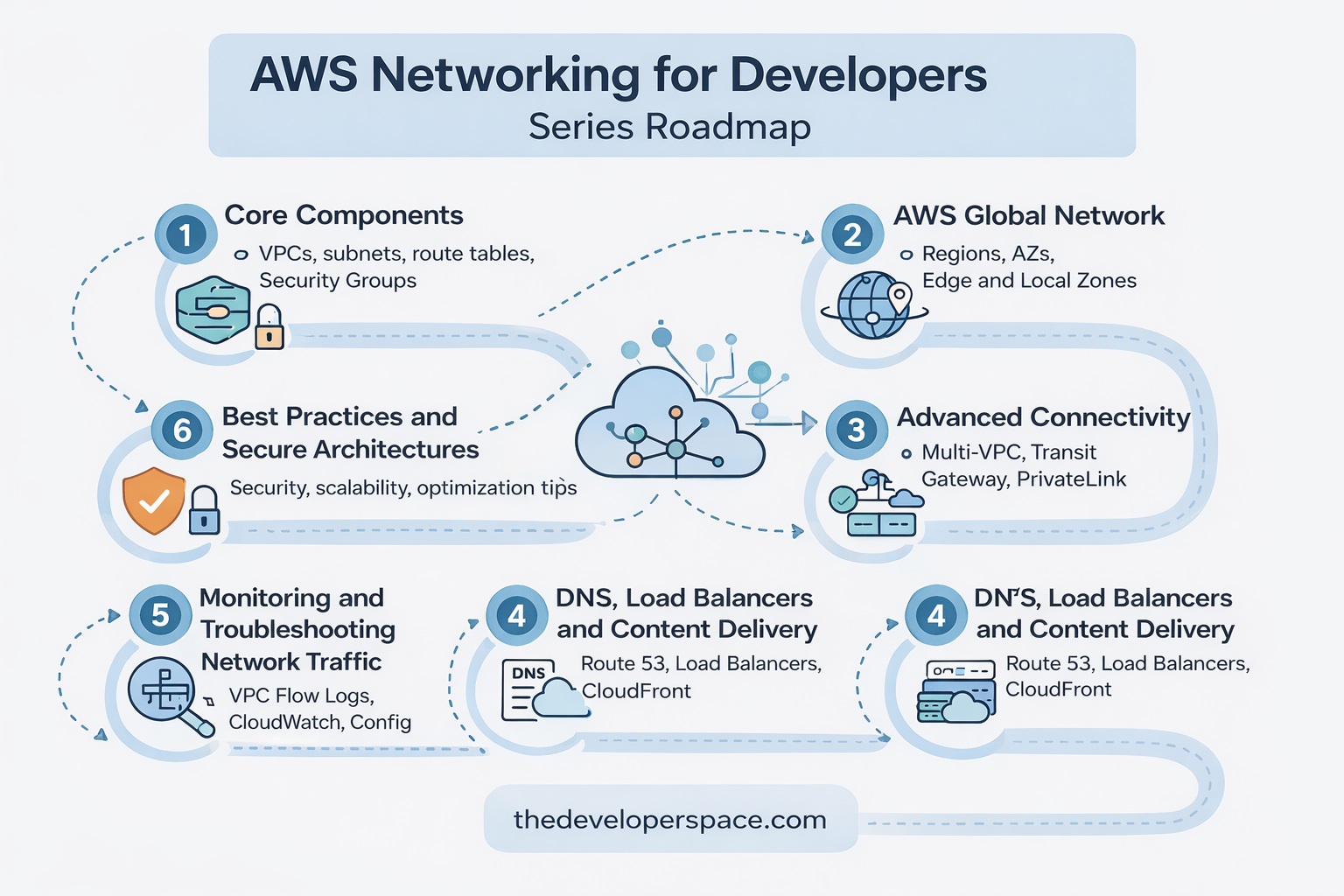
Articles in this series
This is the first installment in a series of articles. Please watch this space for updates and new articles in the series.
![]() AWS Networking for Developers: Part 1 – Core Components
AWS Networking for Developers: Part 1 – Core Components
![]() AWS Networking for Developers: Part 2 – AWS Global Network
AWS Networking for Developers: Part 2 – AWS Global Network
![]() AWS Networking for Developers: Part 3 – Advanced Connectivity
AWS Networking for Developers: Part 3 – Advanced Connectivity
![]() AWS Networking for Developers: Part 4 – DNS, Load Balancers and Content Delivery
AWS Networking for Developers: Part 4 – DNS, Load Balancers and Content Delivery
![]() AWS Networking for Developers: Part 5 – Monitoring and Troubleshooting Tools
AWS Networking for Developers: Part 5 – Monitoring and Troubleshooting Tools
![]() AWS Networking for Developers: Part 6 – Developer Best Practices
AWS Networking for Developers: Part 6 – Developer Best Practices
Why Developers Should Care About AWS Networking
As a developer, you might think networking is for DevOps or infrastructure engineers. But in a cloud-first world, understanding AWS networking basics is essential for:
- Designing secure applications
- Debugging connectivity issues
- Setting up CI/CD pipelines correctly
- Scaling applications efficiently
Mastering the AWS networking stack empowers you to build resilient and performant applications with minimal surprises during deployment.
Amazon VPC: Your Virtual Network on AWS
Amazon VPC is the foundational building block of AWS networking, acting as a logically isolated section of the AWS cloud where developers can launch resources in a virtual network they define. Understanding VPC is crucial for developers because every compute resource, whether it’s an EC2 instance, RDS database, or container – resides within a VPC. It allows fine-grained control over networking, including IP address ranges, routing, and access. VPCs interoperate directly with subnets, route tables, internet gateways, and security groups, forming the core of any application deployment on AWS. Without a clear understanding of VPC architecture, developers may run into issues with connectivity, scalability, and security.
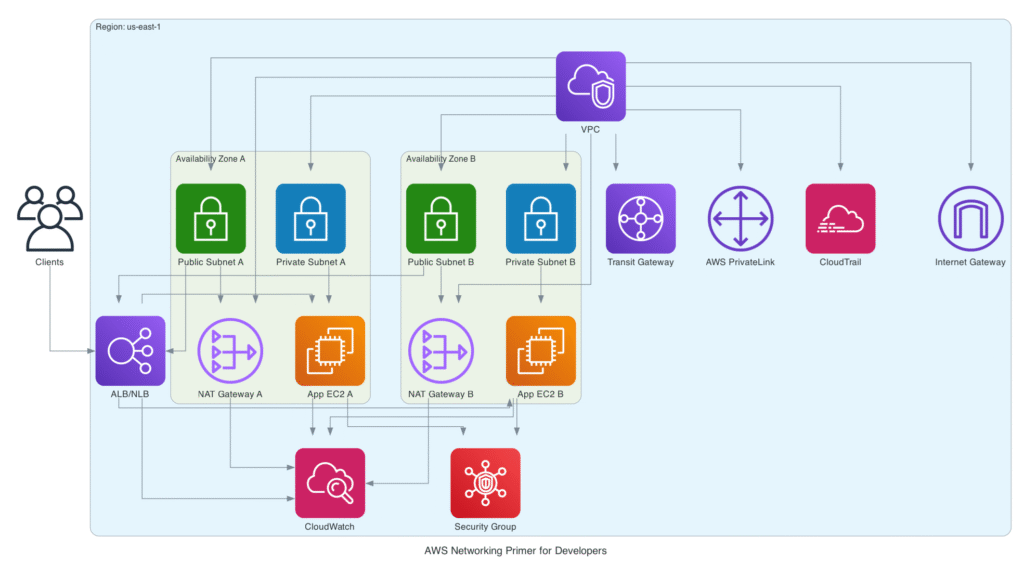
An Amazon VPC is region-specific. There is a default VPC in each region in your AWS account. You can create additional VPCs as needed in each of your regions. When you create a VPC, you choose the AWS region in which it resides (e.g., us-east-1, eu-west-1). All the networking resources you create inside the VPC – such as subnets, route tables, and gateways – must also be within the same region. You cannot span a VPC across multiple regions. This regional scope ensures data locality and simplifies regional network architecture.
CIDRs (Classless Inter-Domain Routing)
CIDR defines a block of IP addresses using a combination of an IP and a subnet mask. For example, 10.0.0.0/16. The /16 indicates how many bits are fixed as the network portion, allowing for 65,536 IP addresses in this block. CIDRs are how AWS VPCs and subnets are allocated their IP space, enabling flexible and efficient use of IP addresses. CIDR allows for the aggregation of multiple IP addresses into a single route, which helps reduce the size of routing tables and improves routing efficiency.
- VPCs are defined using a CIDR block like 10.0.0.0/16.
- Subnets are created by subdividing this block (e.g., 10.0.1.0/24).
- Route tables, Security Groups, and NACLs reference CIDRs to allow or deny traffic.
- CIDRs are crucial in VPC Peering, where overlapping IP ranges are not allowed.
- PrivateLink and Transit Gateway traffic relies on correct CIDR planning to route packets between services and VPCs without collision.
CIDRs are critical when defining your VPC and subnet boundaries. If you misallocate IP ranges, you might run out of usable IPs, block future expansion, or overlap ranges between VPCs, causing routing conflicts. Developers often face deployment issues because of poor CIDR planning. Understanding this helps avoid environment fragmentation and simplifies cross-VPC connectivity.
CIDR Block Reference Table
| CIDR Block | IP Address Range Example | Number of IPs |
|---|---|---|
| /32 | 192.168.1.0 – 192.168.1.0 | 1 |
| /31 | 192.168.1.0 – 192.168.1.1 | 2 |
| /30 | 192.168.1.0 – 192.168.1.3 | 4 |
| /24 | 192.168.1.0 – 192.168.1.255 | 256 |
| /20 | 192.168.0.0 – 192.168.15.255 | 4,096 |
| /16 | 10.0.0.0 – 10.0.255.255 | 65,536 |
| /12 | 172.16.0.0 – 172.31.255.255 | 1,048,576 |
Note: AWS reserves 5 IPs per subnet (first IP = network, last IP = broadcast, and 3 are reserved by AWS), so always account for this when allocating subnets.
Prefix List
A Prefix List is a collection of one or more CIDR blocks grouped together under a single, reusable entity. It acts like a named alias for a set of IP address ranges: either AWS-managed or customer-defined, that can be referenced in security groups, route tables, and network ACLs. AWS supports two types of prefix lists.
AWS-Managed Prefix Lists
AWS-Managed Prefix Lists are maintained by AWS and updated automatically. They represent IP ranges for AWS services like S3, DynamoDB, CloudFront, etc.
Example: com.amazonaws.us-east-1.s3 → contains the IPs used by S3 in the US North Virgina region
Customer-Managed Prefix Lists
Customer-Managed Prefix Lists are created by users to represent on-premises IPs, partner networks, or shared VPCs. They make it easier to manage multiple firewall rules or route table entries across accounts.
Subnets
Subnets are subdivisions of a VPC’s IP address range, enabling developers to logically group resources based on functionality and access requirements.
Subnets are tied to specific Availability Zones within the region of the parent VPC. When creating a subnet, you assign it to one AZ (e.g., us-west-2a). This tight coupling allows developers to distribute resources across multiple AZs for high availability and fault tolerance. A subnet cannot span across multiple AZs or be moved between them.
There are two types of Subnets:
Public Subnets
A public subnet in AWS is a subnet that has a route to an Internet Gateway, allowing resources inside it (like EC2 instances) to communicate directly with the internet. Public subnets are commonly used to host outward-facing services such as web servers, bastion hosts, or load balancers. When you launch an instance in a public subnet and assign it a public IP or Elastic IP, it becomes reachable from the internet – making proper use of Security Groups and Network ACLs essential to avoid exposing vulnerabilities. Developers typically deploy front-end components in public subnets while keeping the rest of the application stack isolated.
Private Subnets
A private subnet, in contrast, is not directly accessible from the internet because it lacks a route to an Internet Gateway. It is used to host backend services like databases, internal APIs, or application servers that shouldn’t be exposed publicly. Instances in a private subnet can still access the internet (for updates or downloading packages) using a NAT Gateway or NAT instance residing in a public subnet. Designing your application with private subnets for sensitive components helps enforce the principle of least exposure, improving overall security posture.
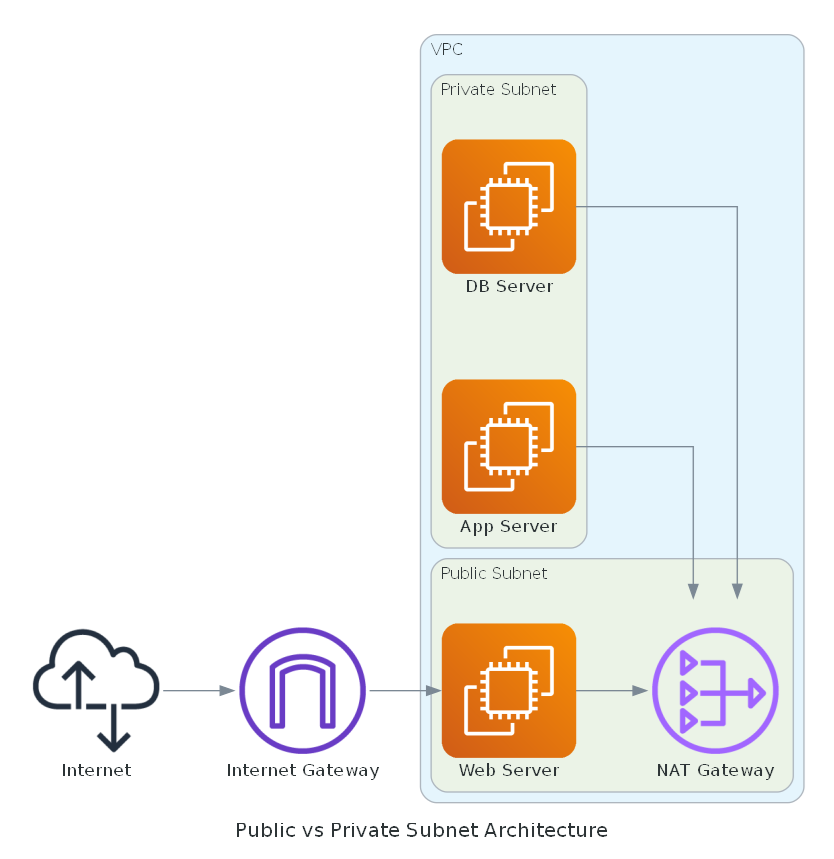
For developers, knowing how to assign resources to the correct subnet ensures that services like RDS, Lambda, and ECS are securely placed and can communicate as intended. Subnets interact with route tables, NAT gateways, and security groups to manage traffic flow and access levels between components.
Recommended Subnet Types for your applications and services
| Application Type | Subnet Type | Notes |
|---|---|---|
| Web Server | Public | Accessed from the Internet by the end users |
| App Server | Private | Accessed by your web apps through local network |
| RDS | Private | Accessed by your services through local network |
DHCP Option Sets
A DHCP Option Set in AWS is a configuration object that defines how instances in your VPC receive DNS and other network configuration details when they boot up, similar to what a traditional DHCP server provides in on-prem environments.
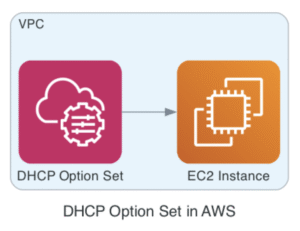
By default, AWS assigns a DHCP option set to your VPC with:
- domain-name-servers:
AmazonProvidedDNS - domain-name: Region-specific (
ec2.internal,us-east-1.compute.internal, etc.)
What It Configures
When an EC2 instance in a VPC starts, it uses the DHCP Option Set to automatically obtain:
| Option | Description |
|---|---|
| domain-name | Default domain name assigned to instances (e.g., ec2.internal) |
| domain-name-servers | IP addresses of DNS servers (AWS default or custom) |
| ntp-servers (optional) | NTP (time sync) servers for instances |
| netbios-name-servers | NetBIOS name resolution (used by older Windows systems) |
| netbios-node-type | Defines NetBIOS behavior on the network |
Why It Matters for Developers
- Automatic DNS Resolution: Instances use these options to resolve hostnames to IP addresses—crucial for service discovery.
- Custom DNS Support: You can point instances to custom DNS servers (e.g., Active Directory, on-prem DNS) instead of AWS-provided ones.
- Centralized Network Config: Instead of manually configuring each EC2, DHCP options apply automatically across subnets.
Route Tables
Route tables define how traffic is directed within a VPC. Each subnet must be associated with a route table, which contains rules mapping IP ranges to destinations such as internet gateways, NAT gateways, VPC peering connections, or transit gateways. Developers should understand route tables to ensure resources can communicate internally and externally as expected. Misconfigured routes are a common cause of unreachable services. Route tables work in tandem with subnets and gateways to control the flow of data, impacting how microservices, APIs, and third-party services interact in a distributed architecture.
- Each subnet is associated with one route table
- Routes can direct traffic to:
- Internet Gateway (IGW)
- NAT Gateway
- VPC Peering
- Transit Gateway
Route Table for a Public Subnet
| Destination | Target | Description |
|---|---|---|
| 10.0.0.0/16 | local | Intra-VPC communication |
| 0.0.0.0/0 | igw-0abc1234def5678 | Routes all internet-bound traffic to IGW |
Route Table for a Private Subnet
| Destination | Target | Description |
|---|---|---|
| 10.0.0.0/16 | local | Intra-VPC communication |
| 0.0.0.0/0 | nat-0abc1234def5678 | Internet-bound traffic via NAT Gateway |
Key Differences:
- In the private subnet, the default route (
0.0.0.0/0) points to a NAT Gateway, not an Internet Gateway. - This allows outbound internet access (e.g., downloading packages) while preventing direct inbound connections from the internet.
Route tables are region-specific, as they belong to a VPC which is bound to a region. Each subnet in the VPC is associated with a route table that dictates how traffic is routed. While the route table itself is not tied to an AZ, it manages routes for subnets that are.
Security Groups
Security Groups act as virtual firewalls at the instance level, controlling inbound and outbound traffic. They are stateful, meaning if you allow an inbound request, the response is automatically allowed. Developers often configure security groups to control which services or IPs can access application components, databases, or admin interfaces. Misconfiguration here can lead to both security vulnerabilities and inaccessible services. Security Groups work alongside subnets, EC2 instances, load balancers, and even Lambda functions running within a VPC.
Security Groups are regional, scoped to the VPC they are created in. They can be applied to resources (like EC2 or Lambda) in any AZ within that region and VPC. This flexibility allows consistent security policies across distributed resources.
Network ACLs (Access Control Lists)
Network ACLs provide an additional layer of security at the subnet level and are stateless, meaning rules must be explicitly defined for both inbound and outbound traffic. For developers, understanding NACLs becomes important when troubleshooting strange connectivity issues or enforcing stricter security requirements across an entire subnet. They interact with subnets and route tables, ensuring only permitted traffic is allowed at a broader level than Security Groups.
Network ACLs are region-specific and tied to a VPC. They operate at the subnet level, which means they indirectly relate to AZs since each subnet exists in one AZ. You can apply a NACL to multiple subnets across different AZs within the same region.
Security Group vs ACL
| Feature | Security Group | Network ACL |
|---|---|---|
| Stateful | Yes | No |
| Rule Type | Allow only | Allow/Deny |
| Applied To | Instances/Resources | Subnets |
Tip: Always start with least-privilege rules and expand based on application needs.
Elastic IPs
Elastic IPs are static public IPv4 addresses that can be associated with EC2 instances, making them accessible from the internet. These are useful when consistent public IPs are required, such as for whitelisting in external systems. Developers must manage EIPs wisely to avoid unnecessary costs or resource limitations. EIPs are commonly used with instances in public subnets, and their accessibility is governed by security groups and route tables.
What Next?
Grasping the core components of AWS networking equips developers with the tools to design secure and structured cloud environments. From segmenting your workloads with subnets to managing traffic flow using security groups and load balancers, each of these components plays a crucial role. With this foundation, you’re now ready to explore the extended network capabilities AWS offers for hybrid architectures and service integrations – which we’ll cover in the next part.


[…] AWS Networking for Developers: Part 1 – Core Components […]
[…] AWS Networking for Developers: Part 1 – Core Components […]
[…] AWS Networking for Developers: Part 1 – Core Components […]
[…] AWS Networking for Developers: Part 1 – Core Components […]
[…] AWS Networking for Developers: Part 1 – Core Components […]