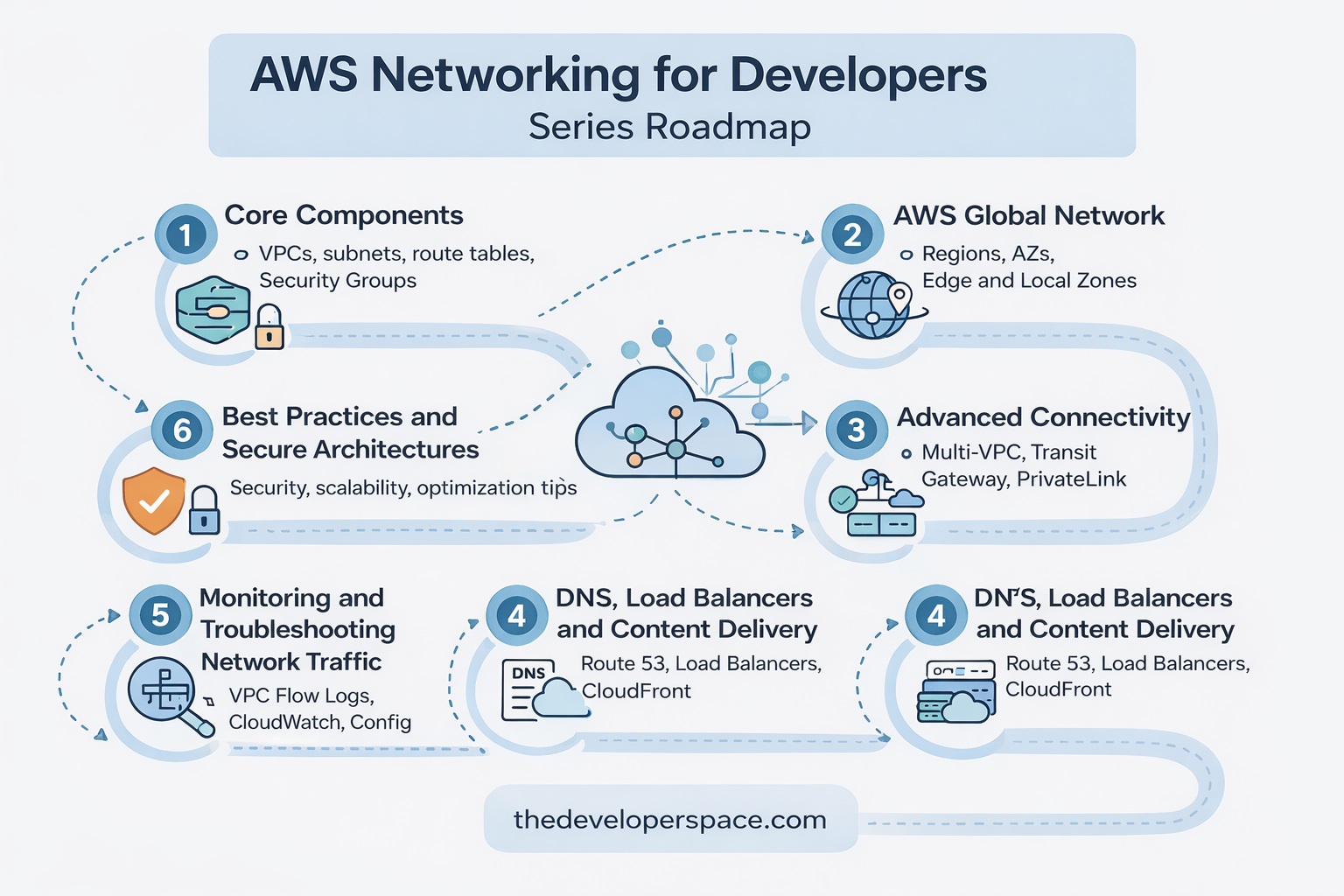
AWS networking can feel overwhelming without a clear learning path. This curated six-part series, AWS Networking for Developers, walks developers step by step from core VPC concepts to advanced connectivity, global infrastructure, monitoring, and real-world best practices—helping you design secure, scalable, and resilient cloud architectures with confidence.